官方github:Releases · kubernetes-sigs/metrics-server (github.com)
v0.7.1安装
1 | kubectl apply -f https://github.com/kubernetes-sigs/metrics-server/releases/download/v0.7.1/components.yaml |
手动安装:
1 | kubectl apply -f - << EOF |
高可用安装:
1 | kubectl apply -f https://github.com/kubernetes-sigs/metrics-server/releases/latest/download/high-availability-1.21+.yaml |
此配置要求群集至少包含 2 个节点,可以在该节点上调度指标服务器
手动安装:
1 | kubectl apply -f - << EOF |
问题排查:
报错:
Failed to scrape node” err=”Get \“https://xx.xx.xx.xx:10250/metrics/resource\“: tls: failed to verify certificate: x509: cannot validate certificate for xx.xx.xx.xx because it doesn’t contain any IP SANs” node=”xxx”
原因:
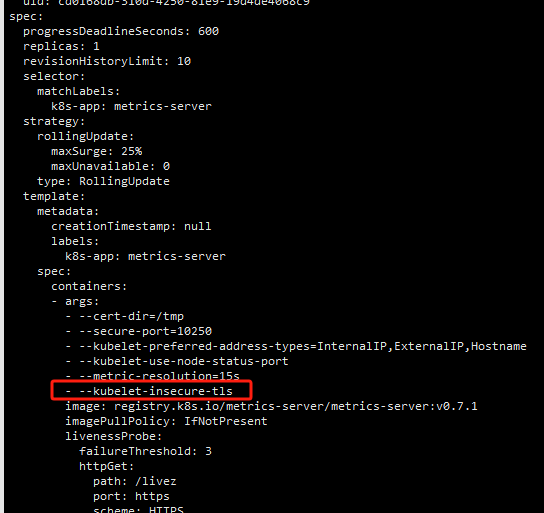
kubelet 的10250端口使用的是https协议,连接需要验证tls证书
1 | kubectl edit deployments.apps -n kube-system metrics-server |
1 | - --kubelet-insecure-tls |