前提条件
cert-manager
ingress-nginx
Helm 2.8.0+
Kubernetes cluster 1.10+
1 | # 命名空间 |
自签名证书
1 | apiVersion: cert-manager.io/v1 |
查看tls文件
1 | [root@k8s-master01 cert-manager]# kubectl get secrets -n devops harbor-selfsigned-secret |
安装Harbor
1 | helm repo add harbor https://helm.goharbor.io |
修改values.yaml
1 | cd ./harbor |
1 | expose: |
中文注释都是改动的位置
安装
1 | helm upgrade --install harbor -n devops . |
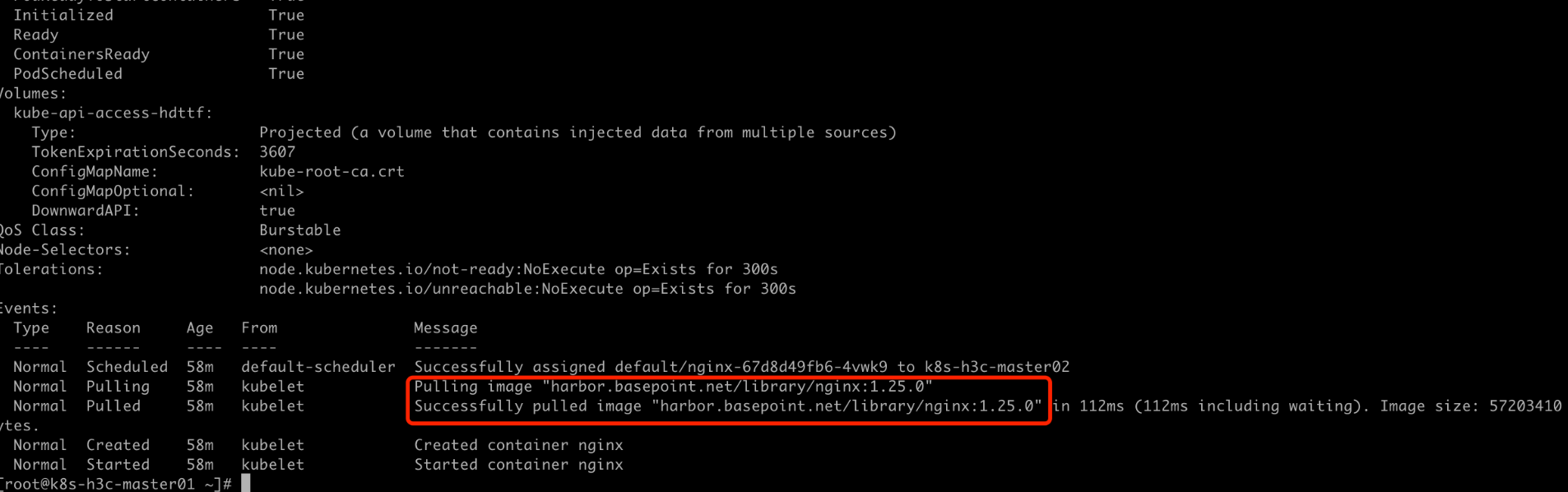
1 | [root@k8s-h3c-master01 ~]# kubectl get pod -n devops |
查看ingress
1 | [root@k8s-h3c-master01 ~]# kubectl get ingress -n devops |
添加hosts
系统添加,略过。
查看证书
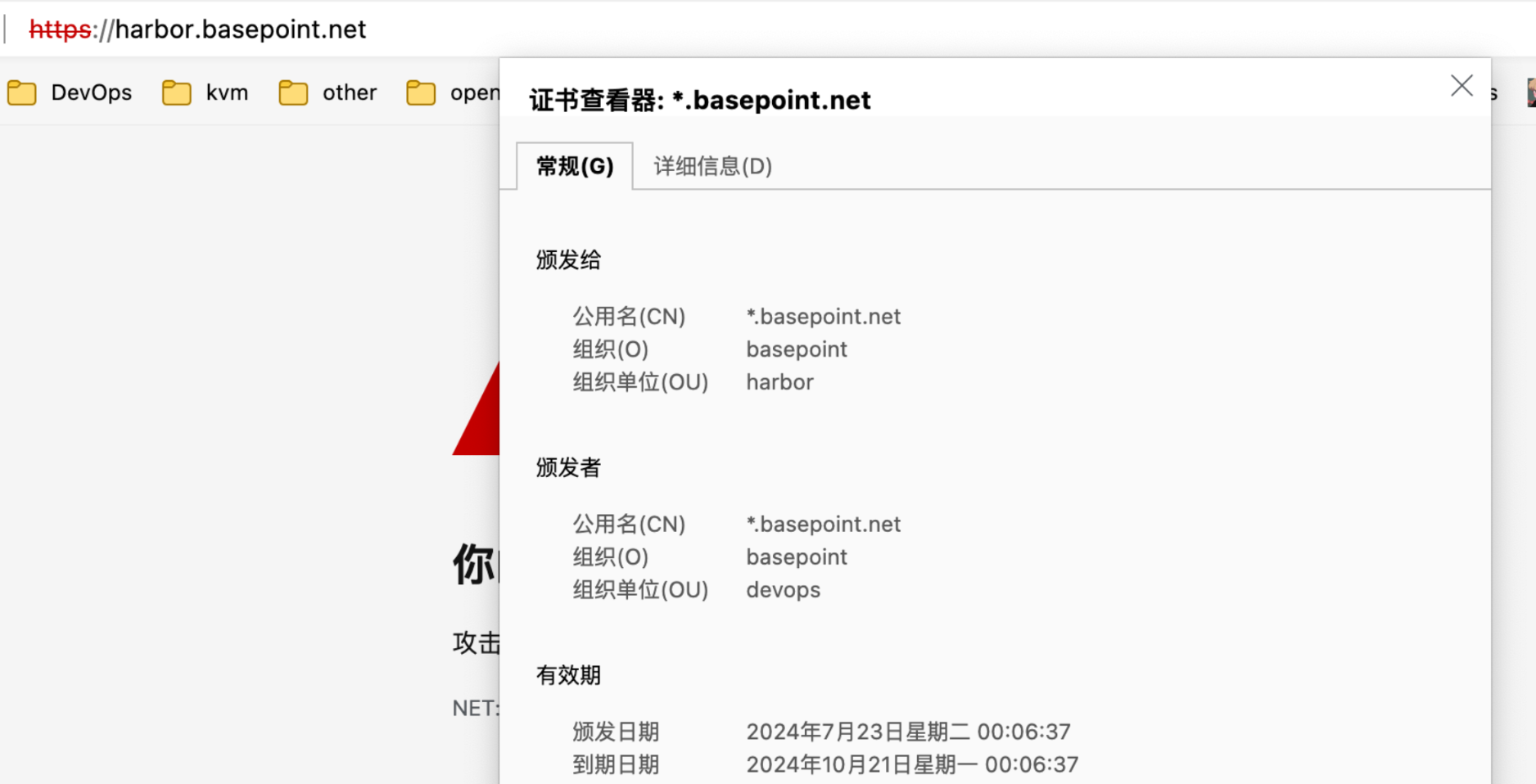
系统颁发证书
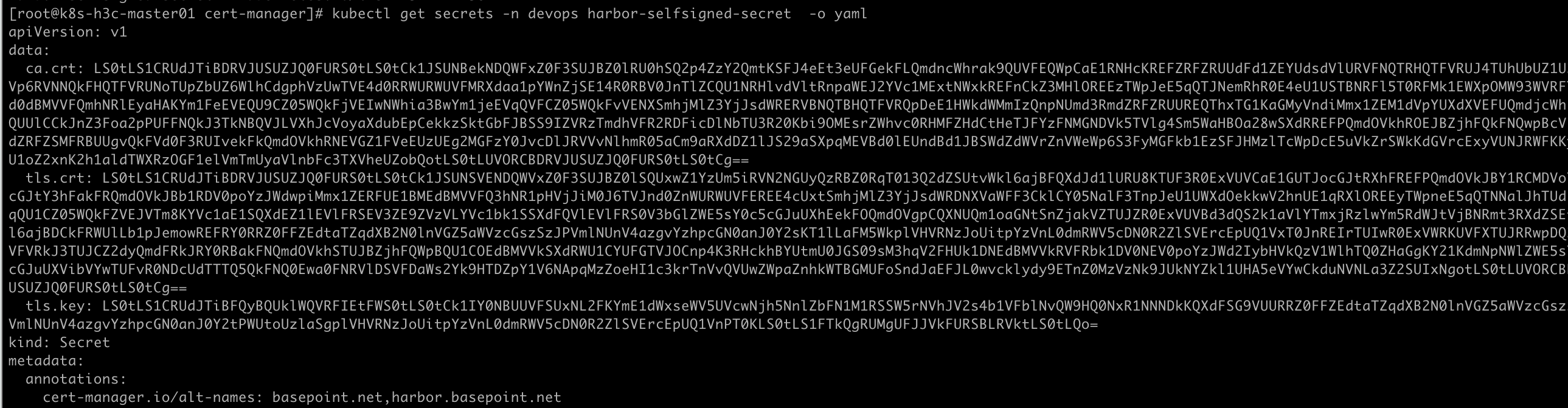
1 | # basse64解码并保存到电脑 |
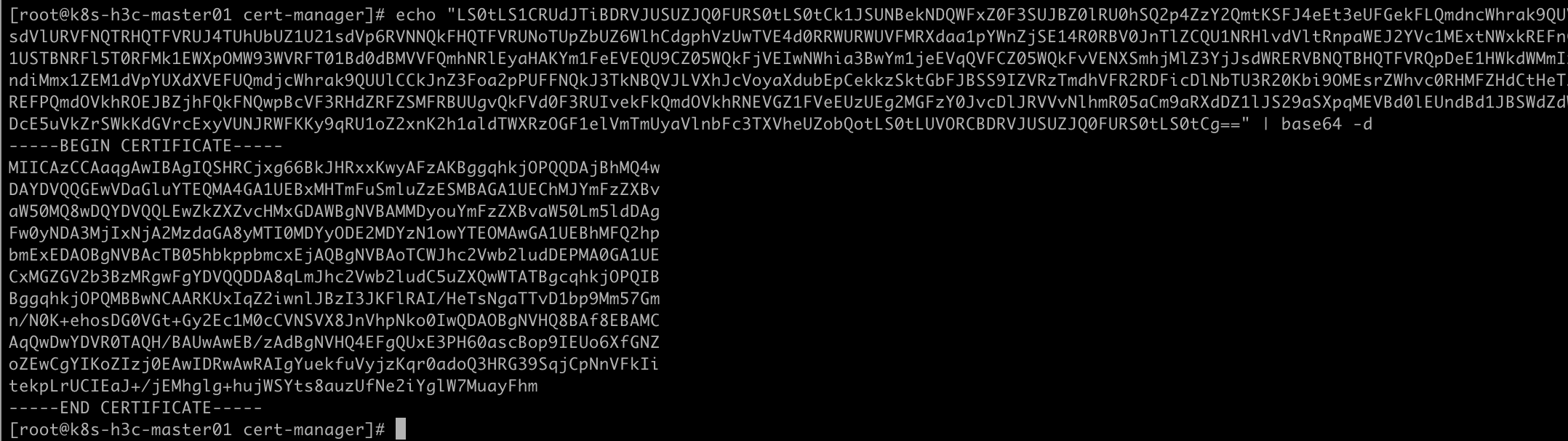
MacOS 导入证书
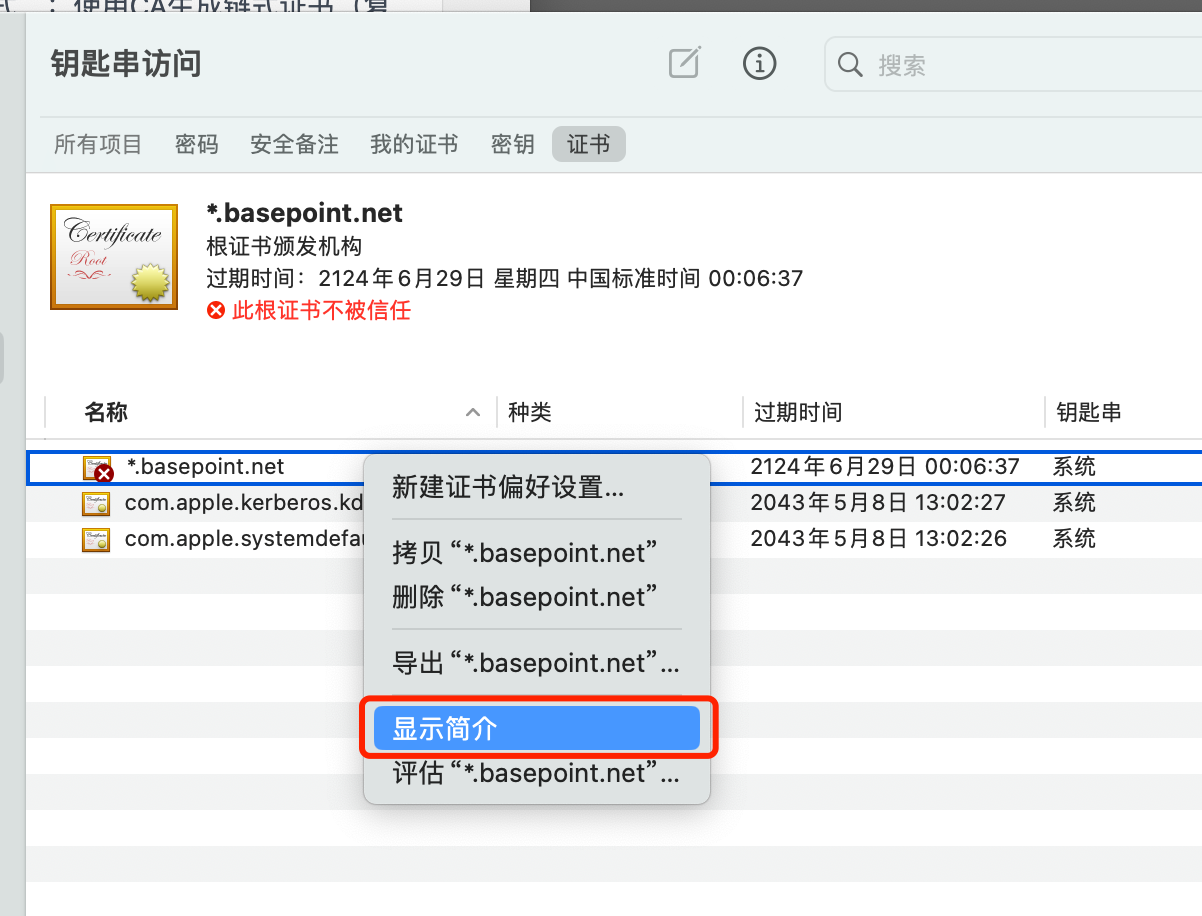
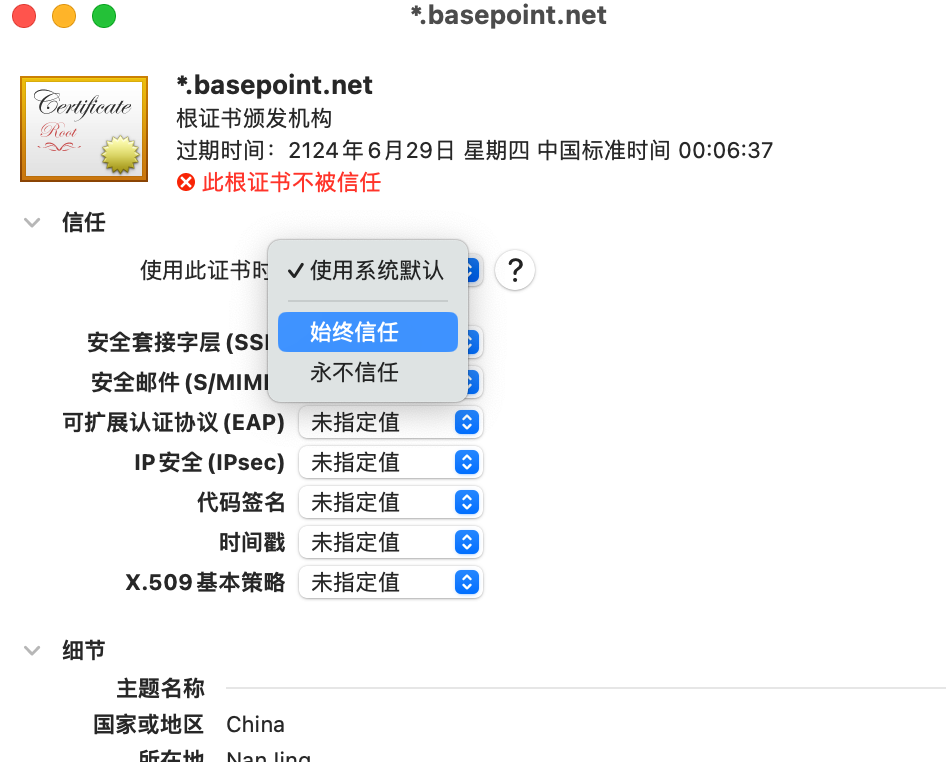
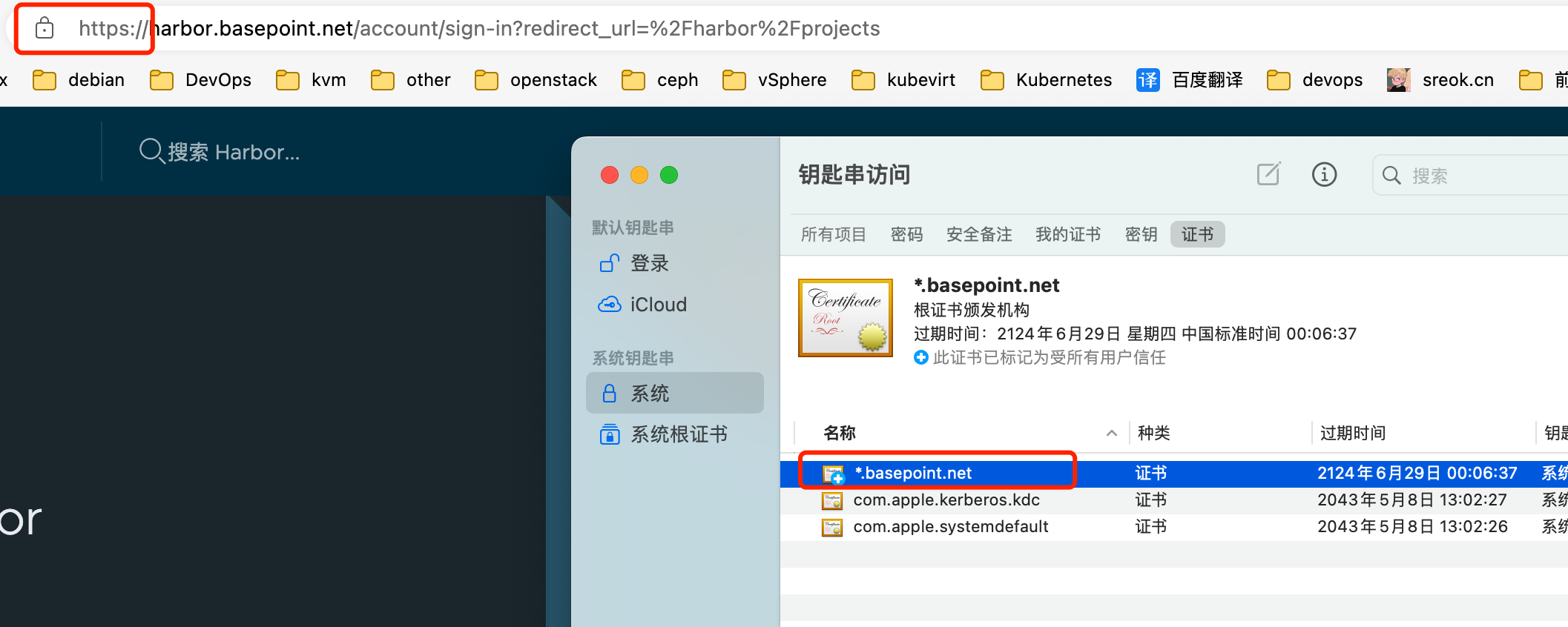
Linux 导入证书(全部k8s节点操作)
安装ca-certificates,一般系统是自带的
1 | yum install ca-certificates |
将证书放置以下目录
1 | /etc/pki/ca-trust/source/anchors/ |
执行信任此证书
1 | update-ca-trust |
此操作会更新以下文件,而不是只是tls-ca-bundle.pem
2
3
4
/etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
/etc/pki/ca-trust/extracted/pem/email-ca-bundle.pem
/etc/pki/ca-trust/extracted/pem/objsign-ca-bundle.pem删除时在
/etc/pki/ca-trust/source/anchors/文件中删掉对应的ca证书,重新执行update-ca-trust即可。
创建imagePullSecrets
方式一:在命令行上提供凭据来创建 Secret
1 | kubectl create secret docker-registry regcred \ |
方式二:创建一个基于现有凭据的 Secret
选择其中一个节点安装docker
1 | yum -y install docker-ce |
登录docker
1 | docker login harbor.basepoint.net -u admin -p Harbor12345 |
登录成功后会创建一个文件:~/.docker/config.json
1 | kubectl create secret generic harbor-admin \ |
测试拉取镜像
将library设置为私有仓库
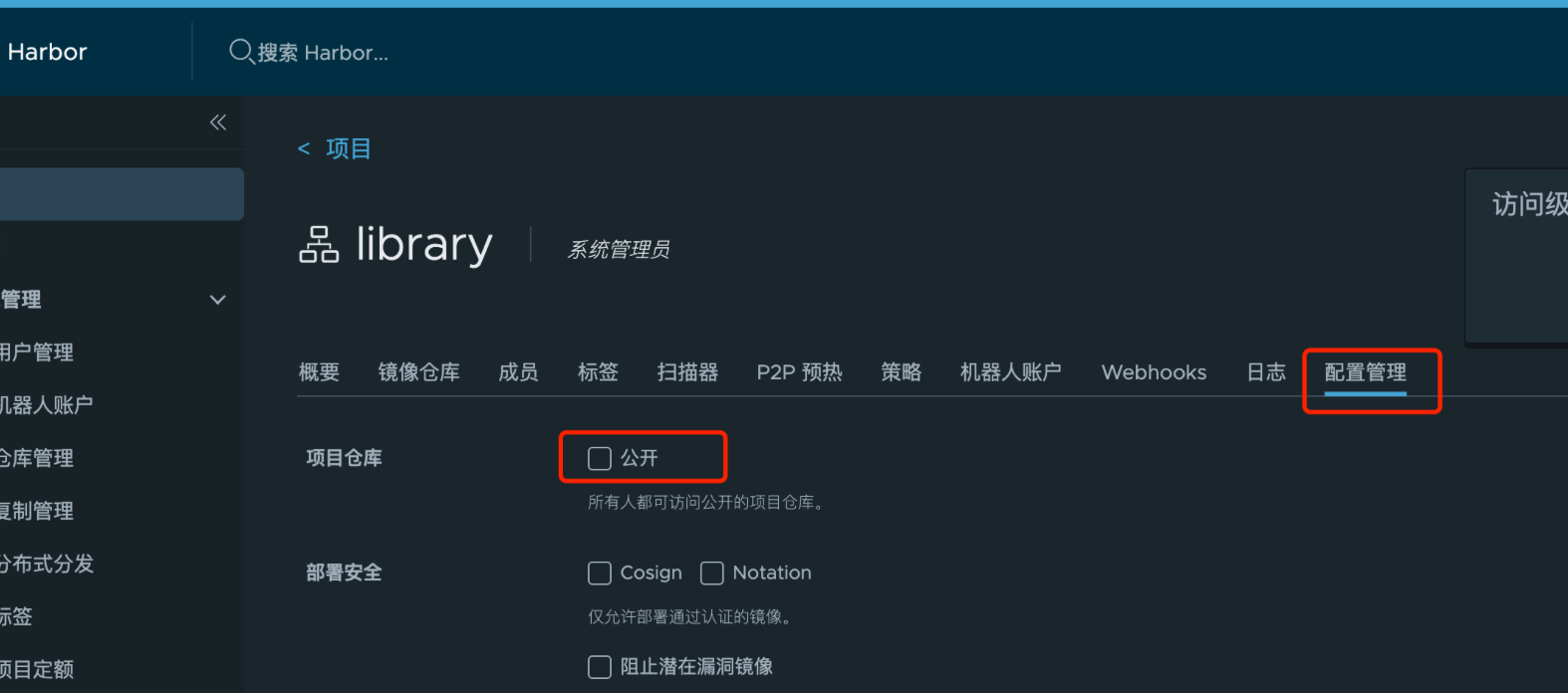
拉取私有仓库镜像
1 | cat > nginx.yaml << EOF |
1 | kubectl apply -f nginx.yaml |
成功即可
1 | [root@k8s-h3c-master01 ~]# kubectl get pod |