自签名证书一般用于服务间或内网访问使用,在公网访问会有不安全提示。
前提条件
k8s集群<1.19
cert-manager
ingress-nginx
方式一:使用自签名作为根证书(简单明了)
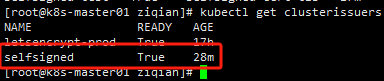
创建ClusterIssuer
1 | apiVersion: cert-manager.io/v1 |
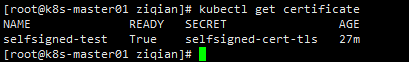
创建证书
1 | apiVersion: cert-manager.io/v1 |
检查证书状态,True即可使用
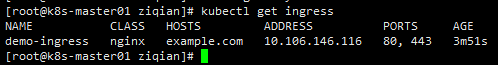
ingress配置
1 | apiVersion: networking.k8s.io/v1 |
方式二:使用CA生成链式证书(复杂、安全)
创建根证书
1 | # 创建根证书 |
颁发CA证书
1 | # 基于CA创建ClusterIssuer |
基于CA颁发TLS证书
1 | --- |
Ingress配置
1 | apiVersion: networking.k8s.io/v1 |
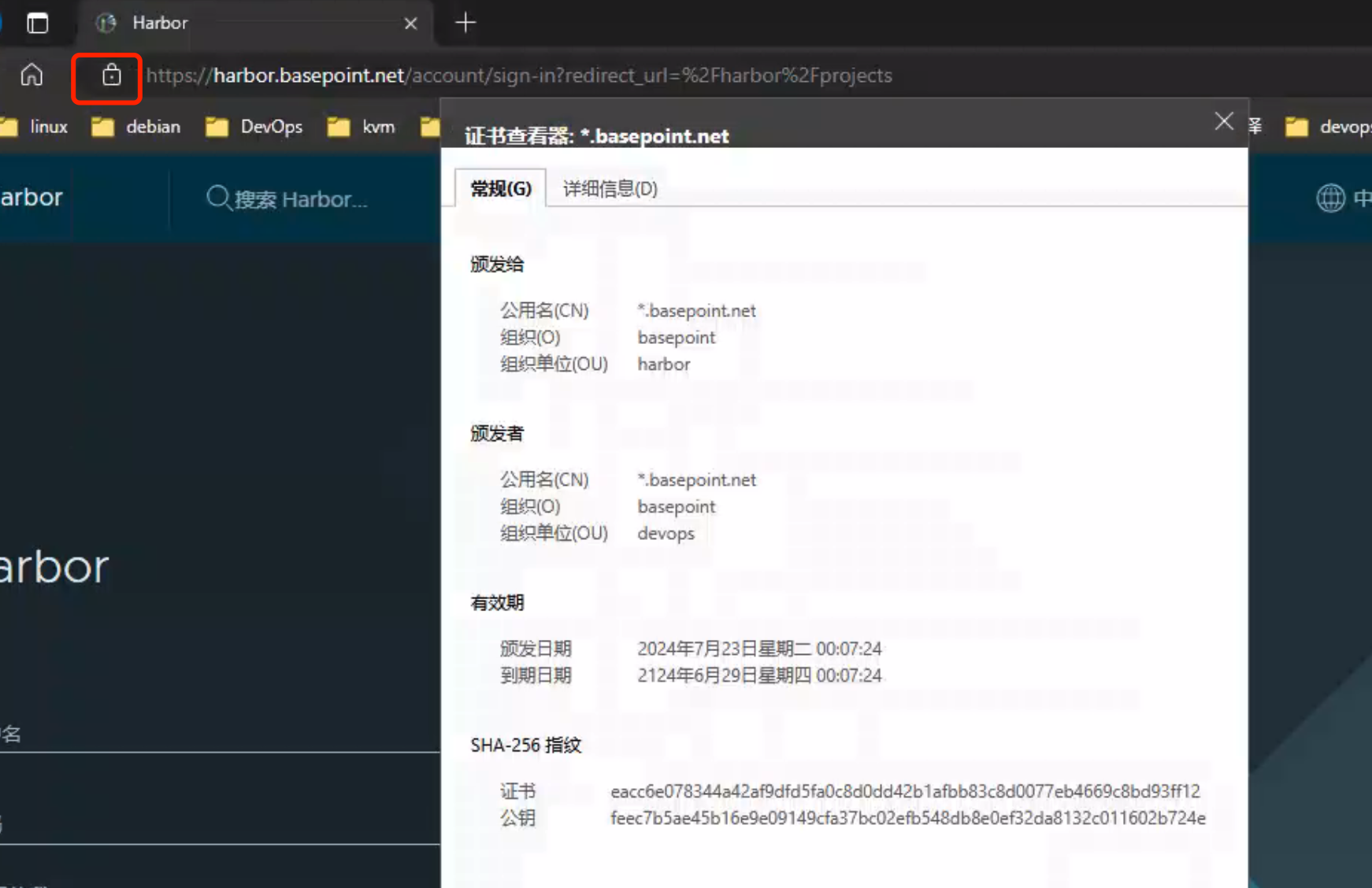
测试(Harbor平台开启TLS认证)
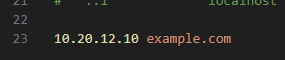
修改hosts文件,浏览器访问域名
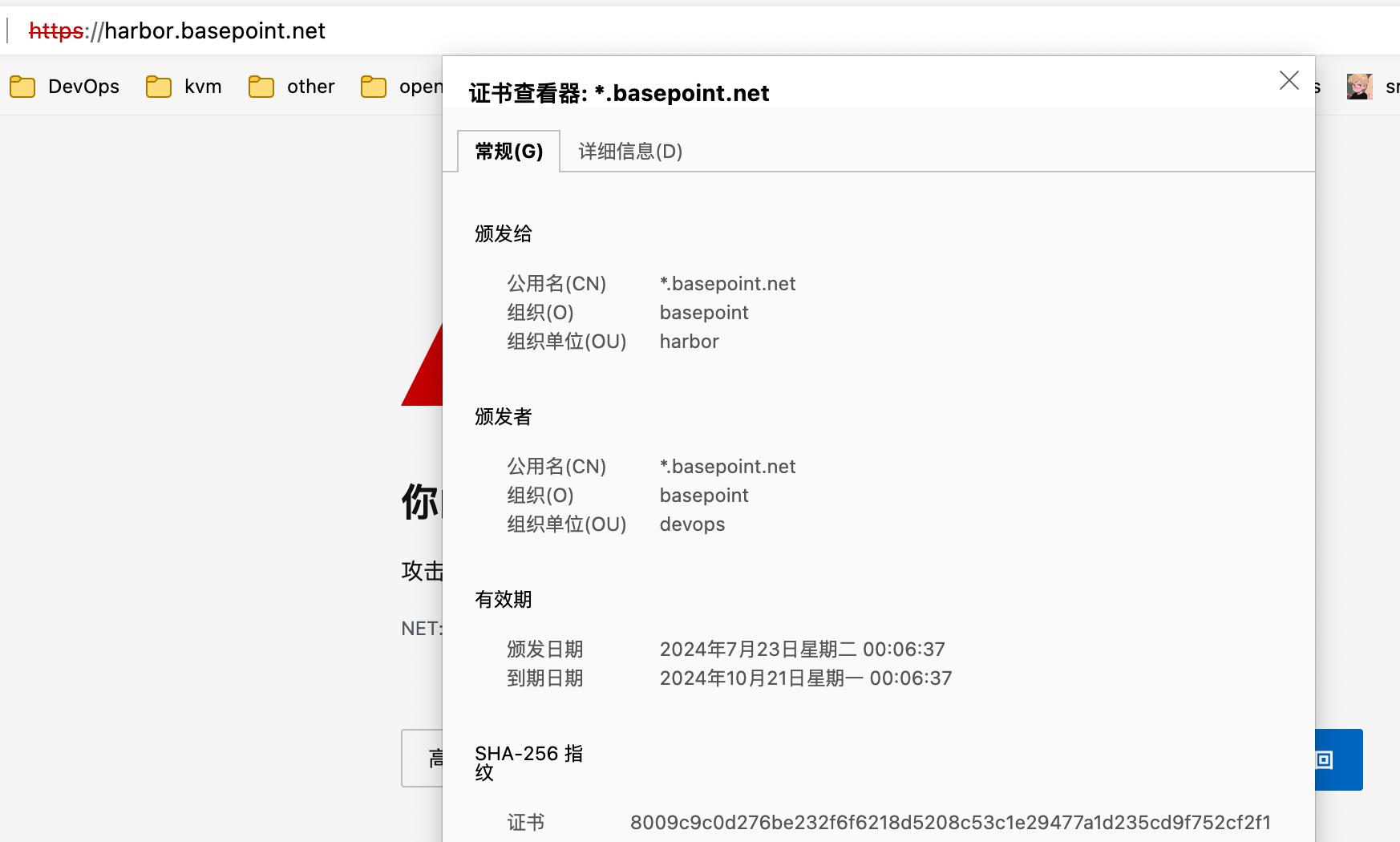
系统颁发证书
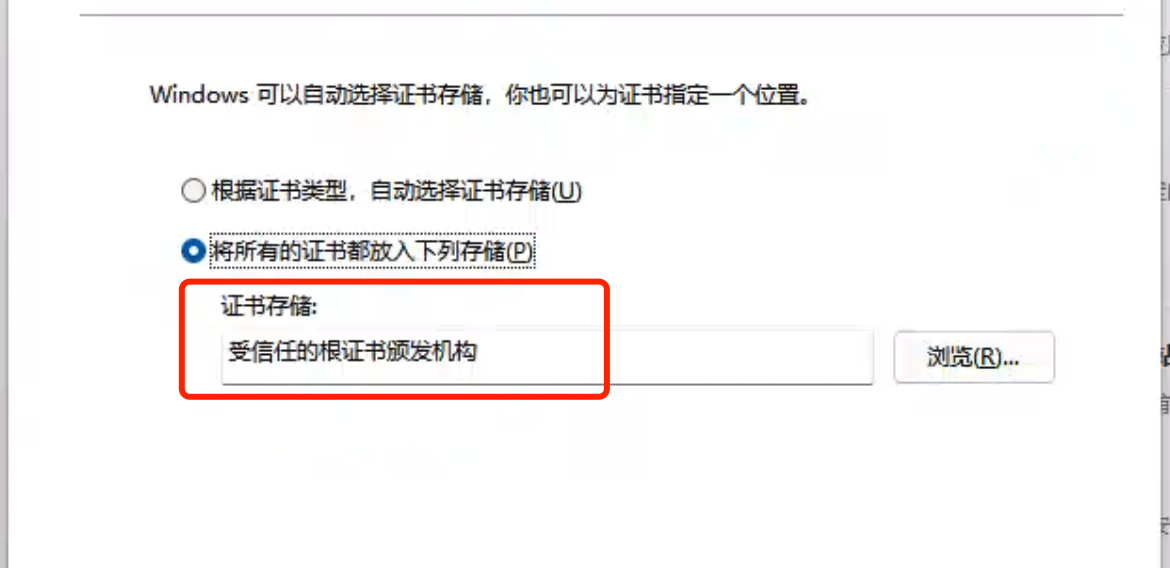
Windows
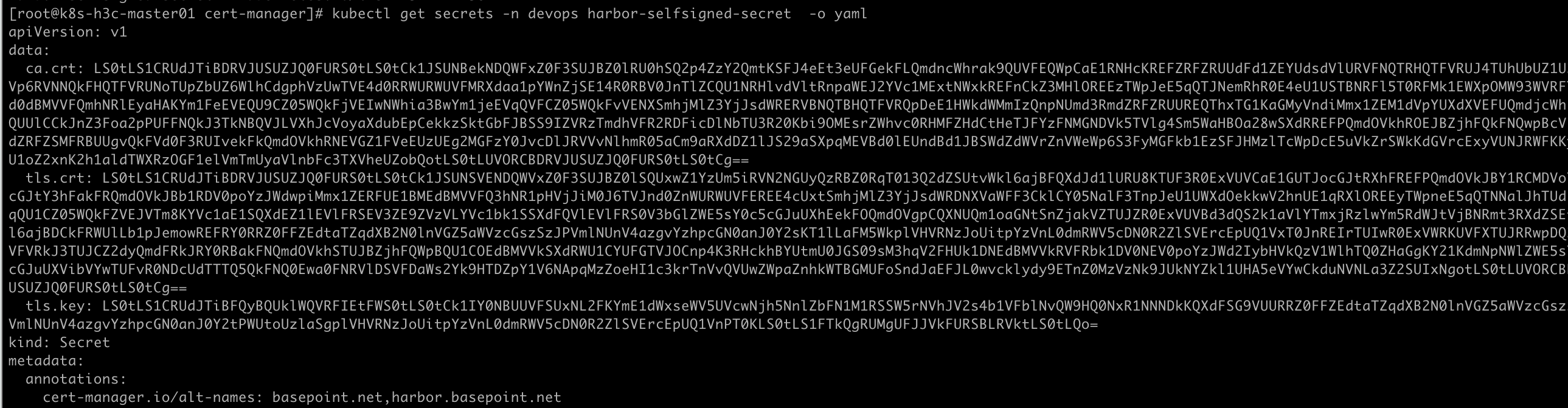
复制ca.crt内容
1 | echo "connect in ca.crt" | base64 -d |
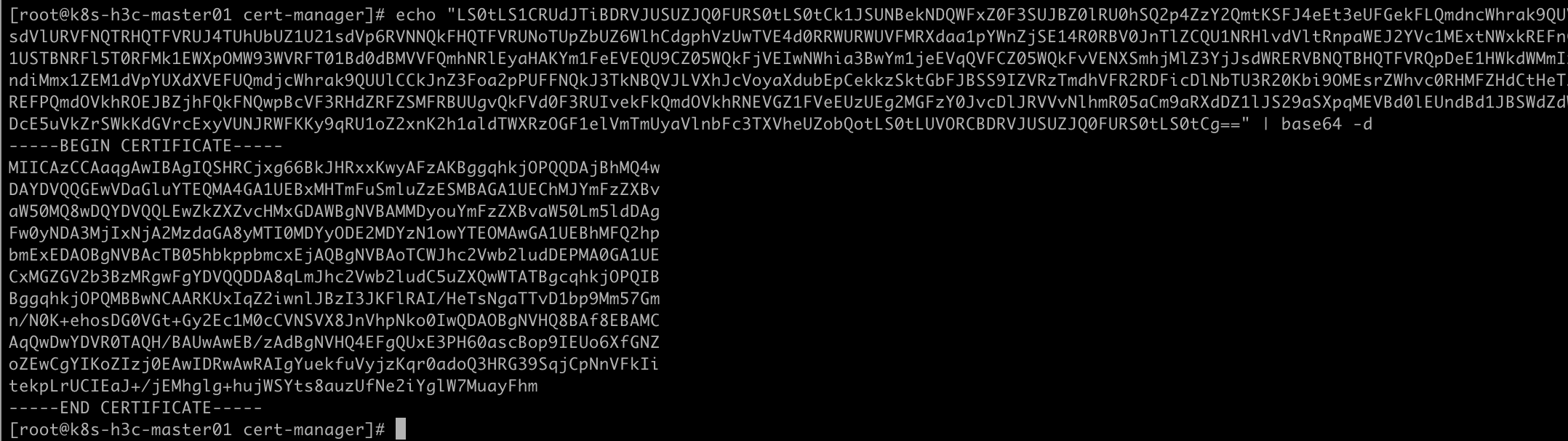
保存到电脑
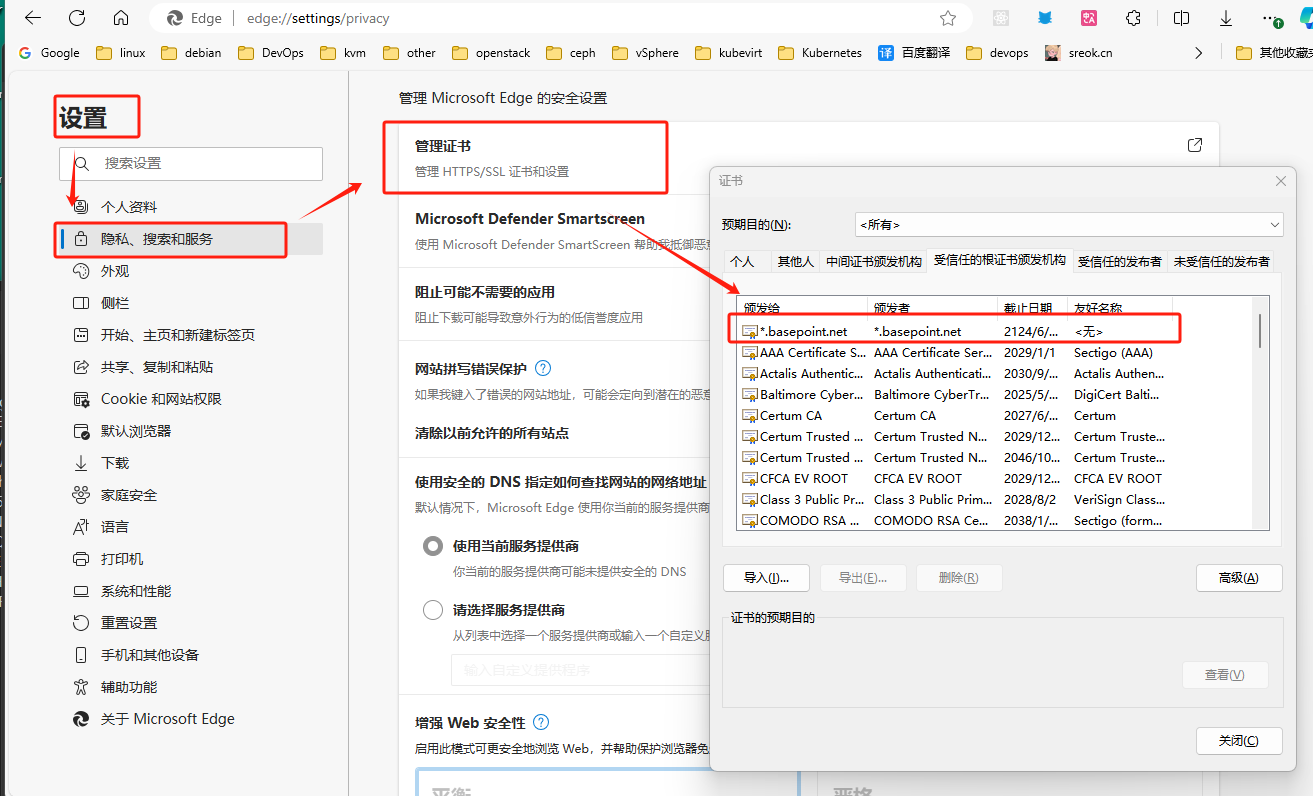
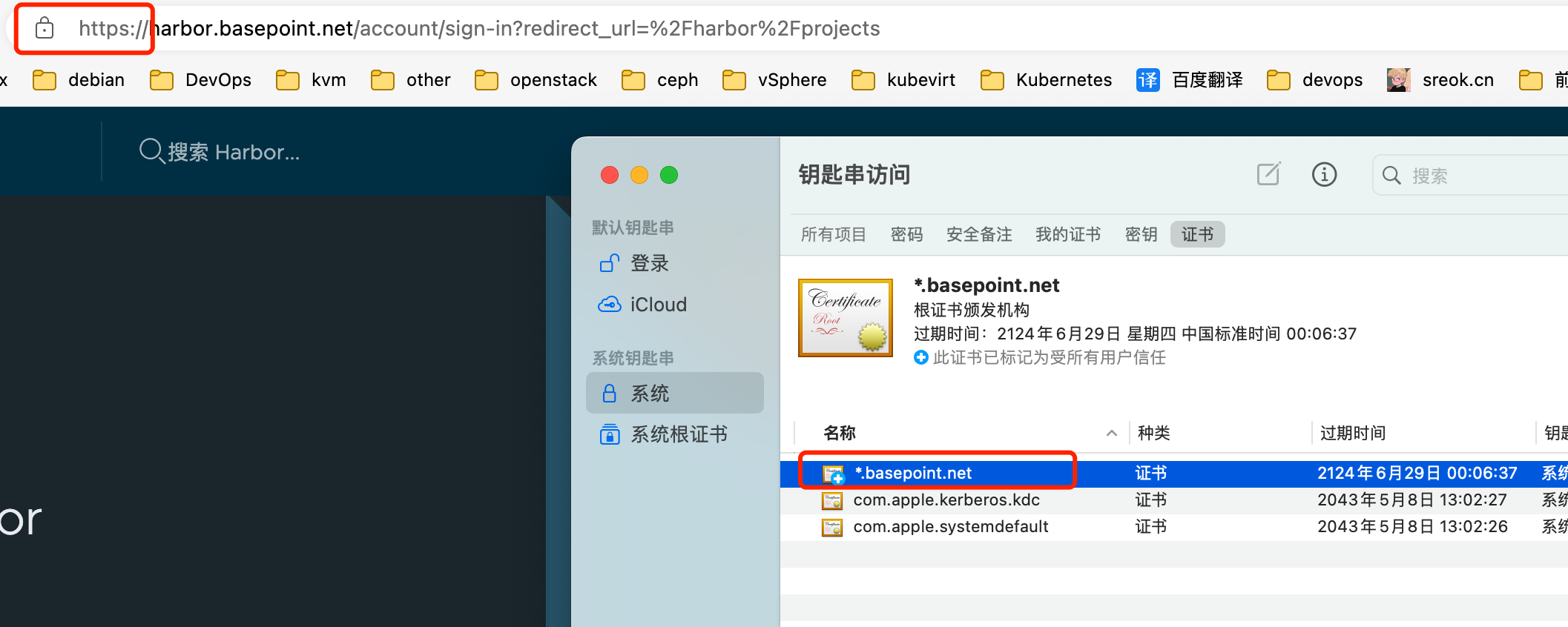
MacOS
双击导入ca.crt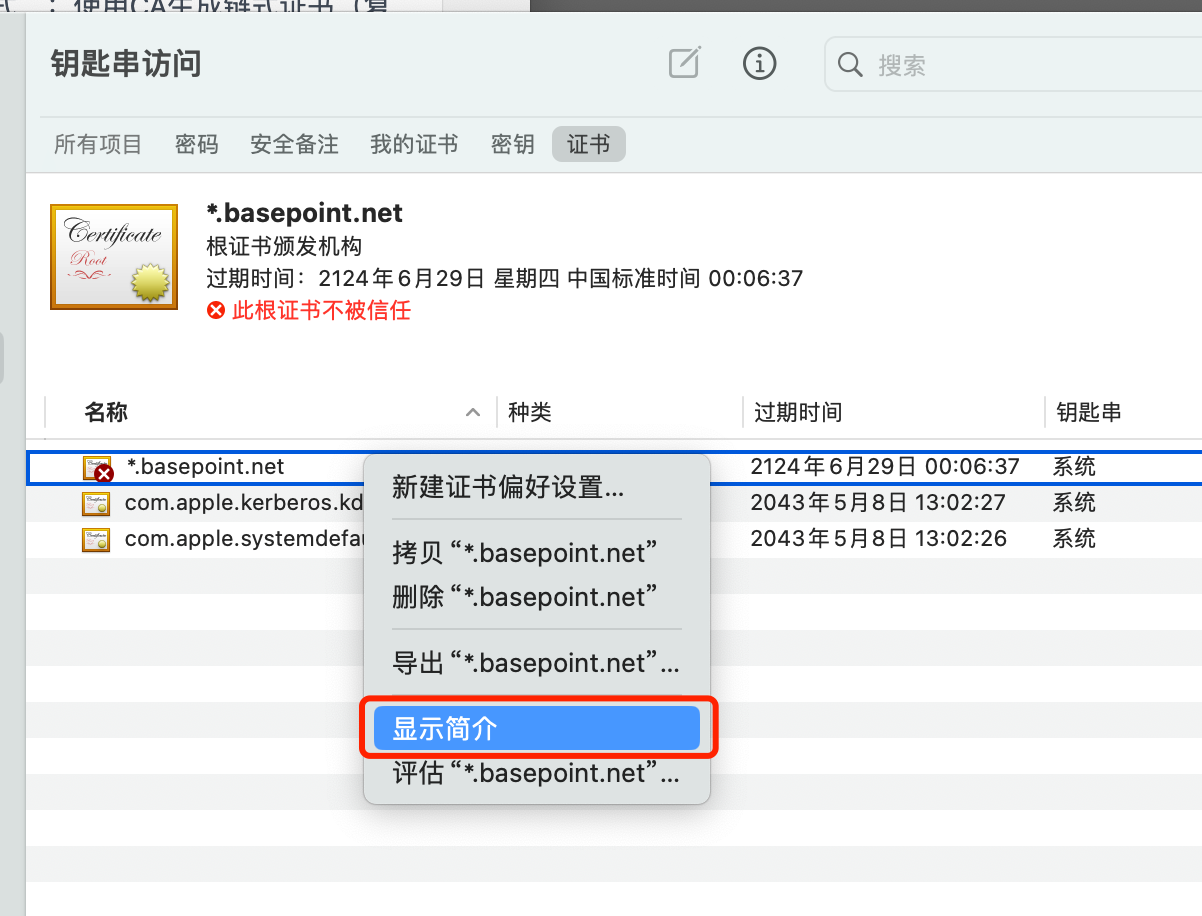
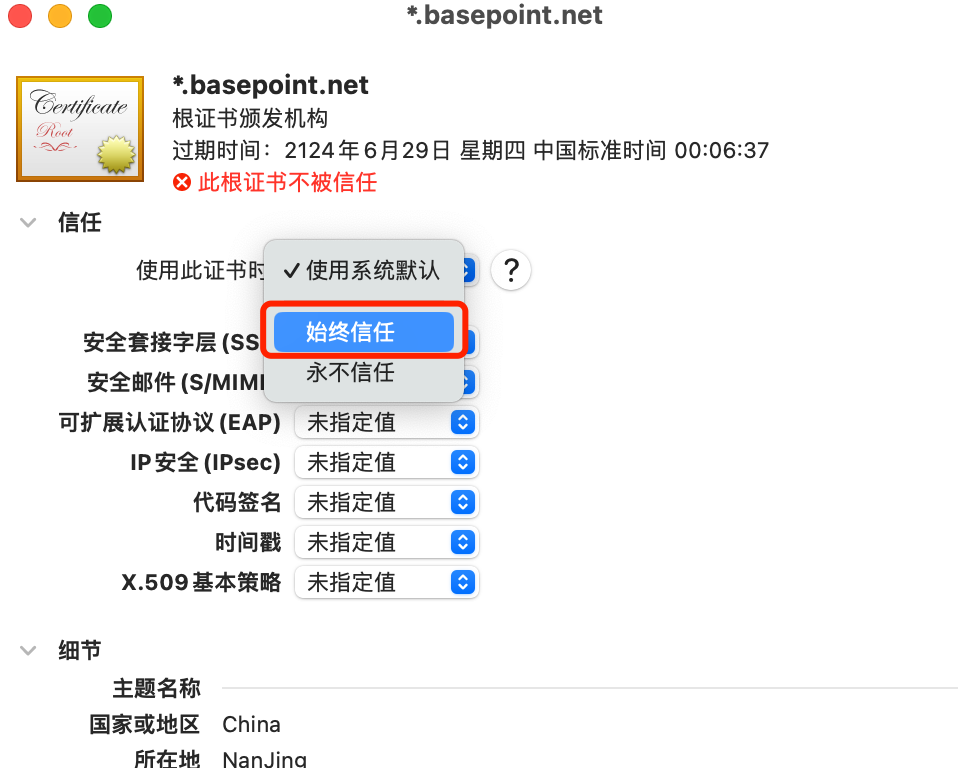
Linux
方法一:只更新TLS证书(简单)
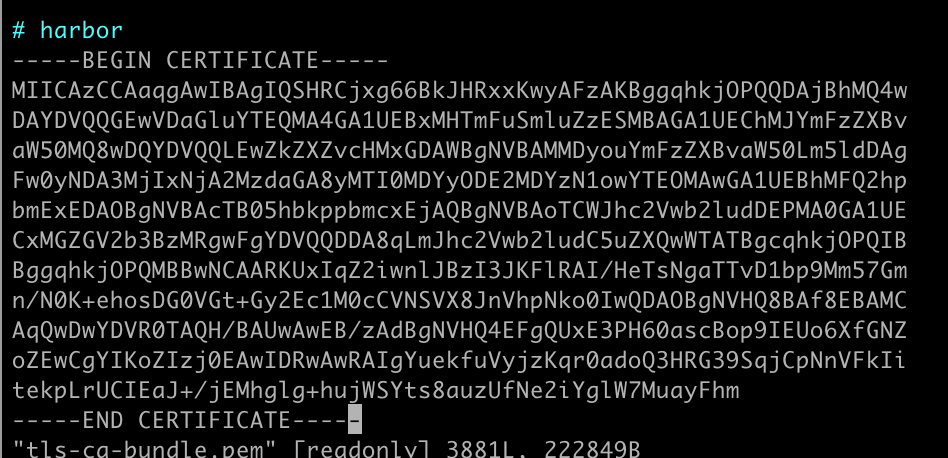
将ca证书追加到以下文件
1 | /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem |
方法二:全部信任此证书
安装ca-certificates,一般系统是自带的
1 | yum install ca-certificates |
将证书放置以下目录
1 | /etc/pki/ca-trust/source/anchors/ |
执行信任此证书
1 | update-ca-trust |
此操作会更新以下文件,而不是只是tls-ca-bundle.pem
2
3
4
/etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
/etc/pki/ca-trust/extracted/pem/email-ca-bundle.pem
/etc/pki/ca-trust/extracted/pem/objsign-ca-bundle.pem删除时在
/etc/pki/ca-trust/source/anchors/文件中删掉对应的ca证书,重新执行update-ca-trust即可。

