安装插件
Kubernetes
GitLab
添加GitLab密钥
1. GitLab ==> 创建jenkins用户
2. 进入jenkins个人中心 ==> 创建token
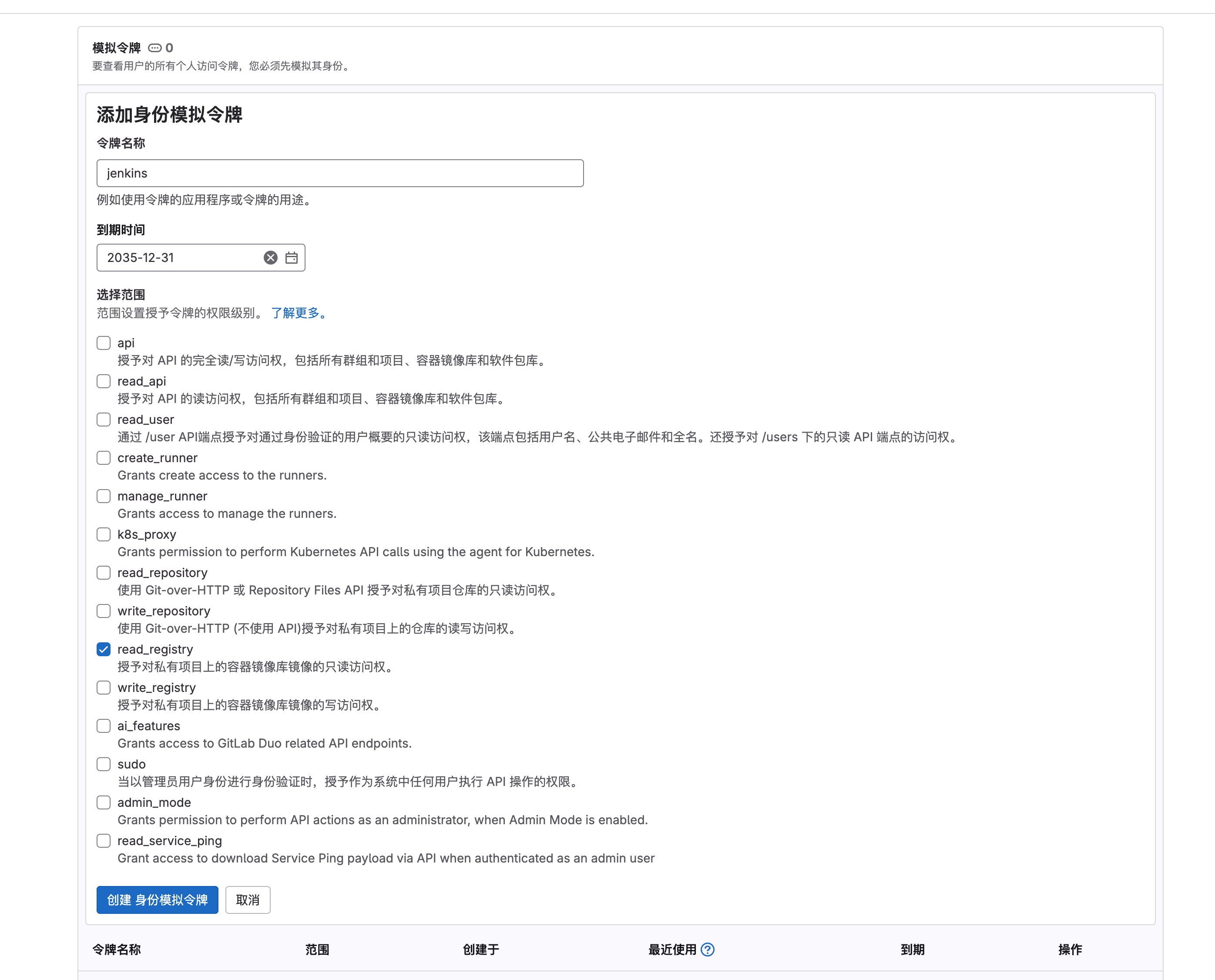
3. jenkins ==> 凭证管理 ==> 系统 ==> 全局凭证 ==> 添加凭证 ==> 类型(GitLab API token)

创建kubernetes凭证(部署用)

自定义构建镜像
FROM rockylinux:9.3
# ca.crt是https的ca证书,用于获取gitlab代码和harbor镜像
COPY ca.crt /etc/pki/ca-trust/source/anchors/
# 部署到kubernetes时使用
COPY kubectl /usr/local/bin
# 部署helm使用
COPY helm /usr/local/bin
# 启动时使用
COPY jenkins-agent /usr/local/bin
# go环境
COPY build/go1.22.5.linux-amd64.tar.gz /tmp
# java环境
COPY build/openjdk-22.0.2_linux-x64_bin.tar.gz /tmp
# workdir时会创建这个目录
WORKDIR /usr/share/jenkins
COPY agent.jar /usr/share/jenkins
# 安装基础包、解压环境、信任证书
RUN yum -y install yum-utils git wget vim && \
tar -C /usr/local -xzf /tmp/go1.22.5.linux-amd64.tar.gz && \
tar -C /usr/local -xzf /tmp/openjdk-22.0.2_linux-x64_bin.tar.gz && \
update-ca-trust
# 设置环境变量
ENV JAVA_HOME=/usr/local/jdk-22.0.2
ENV PATH=$PATH:/usr/local/go/bin:/usr/local/jdk-22.0.2/bin
ENV GOPATH=/usr/share/go
ENV GO111MODULE=on
ENV GOPRIVATE=gitee.cn
ENV GOPROXY=https://goproxy.cn,direct
# 进入镜像时的目录,这里与一会agent要设置的workspaces一致,是为了排查时方便,这个无所谓。
WORKDIR /home/jenkins/agent
ENTRYPOINT ["/usr/local/bin/jenkins-agent"]jenkins-agent最后一行改为:
exec $JAVA_BIN $JAVA_OPTIONS -jar /usr/share/jenkins/agent.jar $SECRET $AGENT_NAME $TUNNEL $URL $WORKDIR $WEB_SOCKET $DIRECT $PROTOCOLS $INSTANCE_IDENTITY "$@"去掉$REMOTING_OPTS,因为启动时jenkins传的参数无效,且用不上。
完整的jenkins-agent脚本
#!/usr/bin/env sh # The MIT License # # Copyright (c) 2015-2020, CloudBees, Inc. # # Permission is hereby granted, free of charge, to any person obtaining a copy # of this software and associated documentation files (the "Software"), to deal # in the Software without restriction, including without limitation the rights # to use, copy, modify, merge, publish, distribute, sublicense, and/or sell # copies of the Software, and to permit persons to whom the Software is # furnished to do so, subject to the following conditions: # # The above copyright notice and this permission notice shall be included in # all copies or substantial portions of the Software. # # THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR # IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, # FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE # AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER # LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, # OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN # THE SOFTWARE. # Usage jenkins-agent.sh [options] -url http://jenkins -secret [SECRET] -name [AGENT_NAME] # Optional environment variables : # * JENKINS_JAVA_BIN : Java executable to use instead of the default in PATH or obtained from JAVA_HOME # * JENKINS_JAVA_OPTS : Java Options to use for the remoting process, otherwise obtained from JAVA_OPTS # * REMOTING_OPTS : Generic way to pass additional CLI options to agent.jar (see -help) # # Deprecated environment variables (prefer setting REMOTING_OPTS) # * JENKINS_TUNNEL : HOST:PORT for a tunnel to route TCP traffic to jenkins host, when jenkins can't be directly accessed over network # * JENKINS_URL : alternate jenkins URL # * JENKINS_SECRET : agent secret, if not set as an argument # * JENKINS_AGENT_NAME : agent name, if not set as an argument # * JENKINS_AGENT_WORKDIR : agent work directory, if not set by optional parameter -workDir # * JENKINS_WEB_SOCKET: true if the connection should be made via WebSocket rather than TCP # * JENKINS_DIRECT_CONNECTION: Connect directly to this TCP agent port, skipping the HTTP(S) connection parameter download. # Value: "<HOST>:<PORT>" # * JENKINS_INSTANCE_IDENTITY: The base64 encoded InstanceIdentity byte array of the Jenkins controller. When this is set, # the agent skips connecting to an HTTP(S) port for connection info. # * JENKINS_PROTOCOLS: Specify the remoting protocols to attempt when instanceIdentity is provided. if [ $# -eq 1 ] && [ "${1#-}" = "$1" ] ; then # if `docker run` only has one arguments and it is not an option as `-help`, we assume user is running alternate command like `bash` to inspect the image exec "$@" else # if -tunnel is not provided, try env vars case "$@" in *"-tunnel "*) ;; *) if [ ! -z "$JENKINS_TUNNEL" ]; then TUNNEL="-tunnel $JENKINS_TUNNEL" fi ;; esac # if -workDir is not provided, try env vars if [ ! -z "$JENKINS_AGENT_WORKDIR" ]; then case "$@" in *"-workDir"*) echo "Warning: Work directory is defined twice in command-line arguments and the environment variable" ;; *) WORKDIR="-workDir $JENKINS_AGENT_WORKDIR" ;; esac fi if [ -n "$JENKINS_URL" ]; then URL="-url $JENKINS_URL" fi if [ -n "$JENKINS_NAME" ]; then JENKINS_AGENT_NAME="$JENKINS_NAME" fi if [ "$JENKINS_WEB_SOCKET" = true ]; then WEB_SOCKET=-webSocket fi if [ -n "$JENKINS_PROTOCOLS" ]; then PROTOCOLS="-protocols $JENKINS_PROTOCOLS" fi if [ -n "$JENKINS_DIRECT_CONNECTION" ]; then DIRECT="-direct $JENKINS_DIRECT_CONNECTION" fi if [ -n "$JENKINS_INSTANCE_IDENTITY" ]; then INSTANCE_IDENTITY="-instanceIdentity $JENKINS_INSTANCE_IDENTITY" fi if [ "$JENKINS_JAVA_BIN" ]; then JAVA_BIN="$JENKINS_JAVA_BIN" else # if java home is defined, use it JAVA_BIN="java" if [ "$JAVA_HOME" ]; then JAVA_BIN="$JAVA_HOME/bin/java" fi fi if [ "$JENKINS_JAVA_OPTS" ]; then JAVA_OPTIONS="$JENKINS_JAVA_OPTS" else # if JAVA_OPTS is defined, use it if [ "$JAVA_OPTS" ]; then JAVA_OPTIONS="$JAVA_OPTS" fi fi # if both required options are defined, do not pass the parameters if [ -n "$JENKINS_SECRET" ]; then case "$@" in *"${JENKINS_SECRET}"*) echo "Warning: SECRET is defined twice in command-line arguments and the environment variable" ;; *) SECRET="-secret ${JENKINS_SECRET}" ;; esac fi if [ -n "$JENKINS_AGENT_NAME" ]; then case "$@" in *"${JENKINS_AGENT_NAME}"*) echo "Warning: AGENT_NAME is defined twice in command-line arguments and the environment variable" ;; *) AGENT_NAME="-name ${JENKINS_AGENT_NAME}" ;; esac fi #TODO: Handle the case when the command-line and Environment variable contain different values. #It is fine it blows up for now since it should lead to an error anyway. #exec $JAVA_BIN $JAVA_OPTIONS -jar /usr/share/jenkins/agent.jar $SECRET $AGENT_NAME $TUNNEL $URL $WORKDIR $WEB_SOCKET $DIRECT $PROTOCOLS $INSTANCE_IDENTITY $REMOTING_OPTS "$@" exec $JAVA_BIN $JAVA_OPTIONS -jar /usr/share/jenkins/agent.jar $SECRET $AGENT_NAME $TUNNEL $URL $WORKDIR $WEB_SOCKET $DIRECT $PROTOCOLS $INSTANCE_IDENTITY "$@" fi
# 构建镜像
docker build -t harbor.basepoint.net/library/rocky_build:jdk22-go1.22.5 .
# 上传私有仓库
docker push harbor.basepoint.net/library/rocky_build:jdk22-go1.22.5(可选)docker dind镜像上传到私有仓库,加速构建时下载镜像
docker pull docker:dind
docker tag docker:dind harbor.basepoint.net/library/docker:dind
docker push harbor.basepoint.net/library/docker:dind创建云节点
Jenkins ==> 系统管理 ==> CLouds ==> New cloud
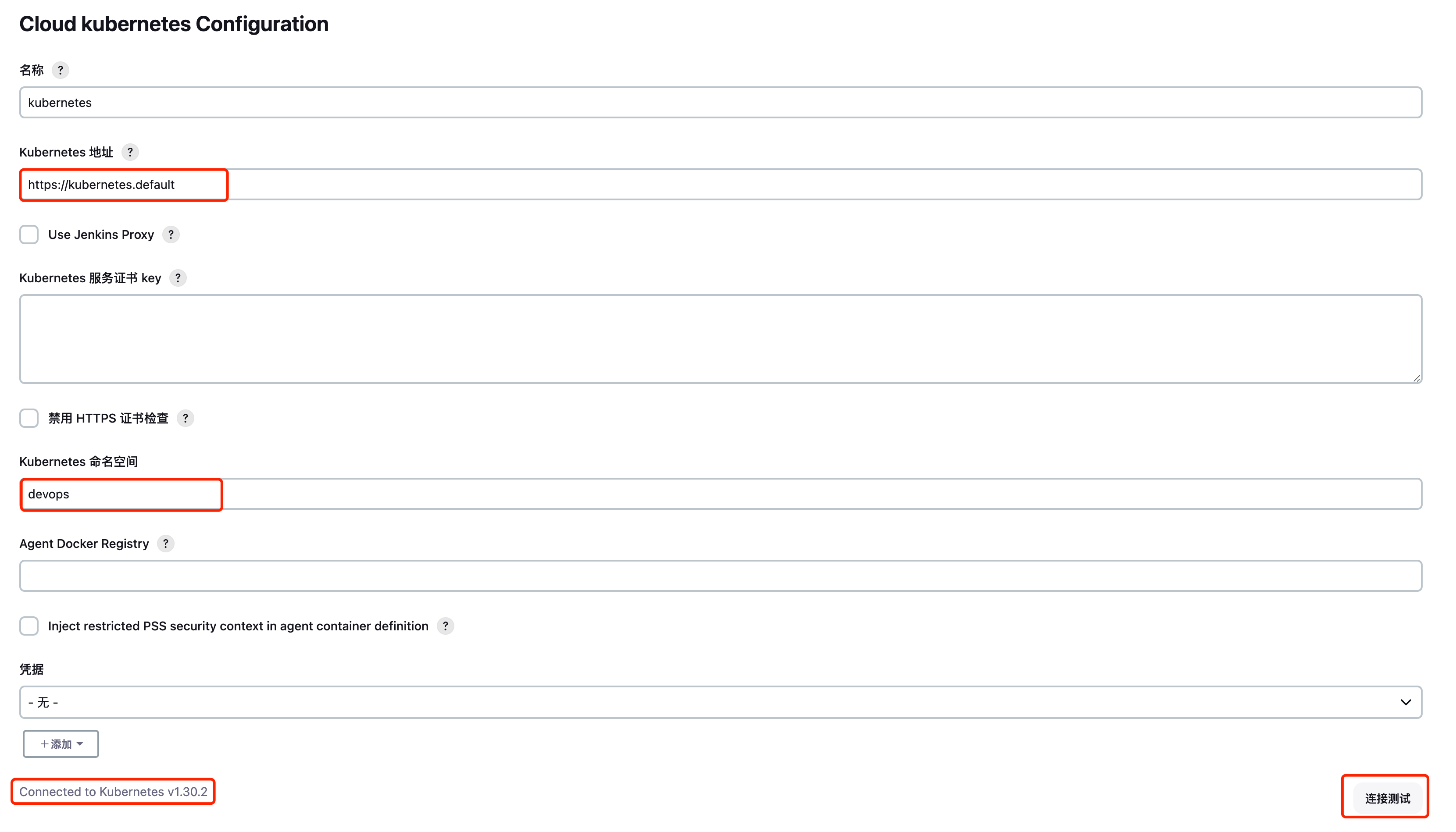

创建Pod模版

名称不设置默认也是jenkins-agent,
命名空间写构建时运行的命名空间,我这里是jenkins在同一个命名空间下(前提RBAC权限要赋予到位)
标签列表,pipline选择节点标签一致时才会触发这个pod模版
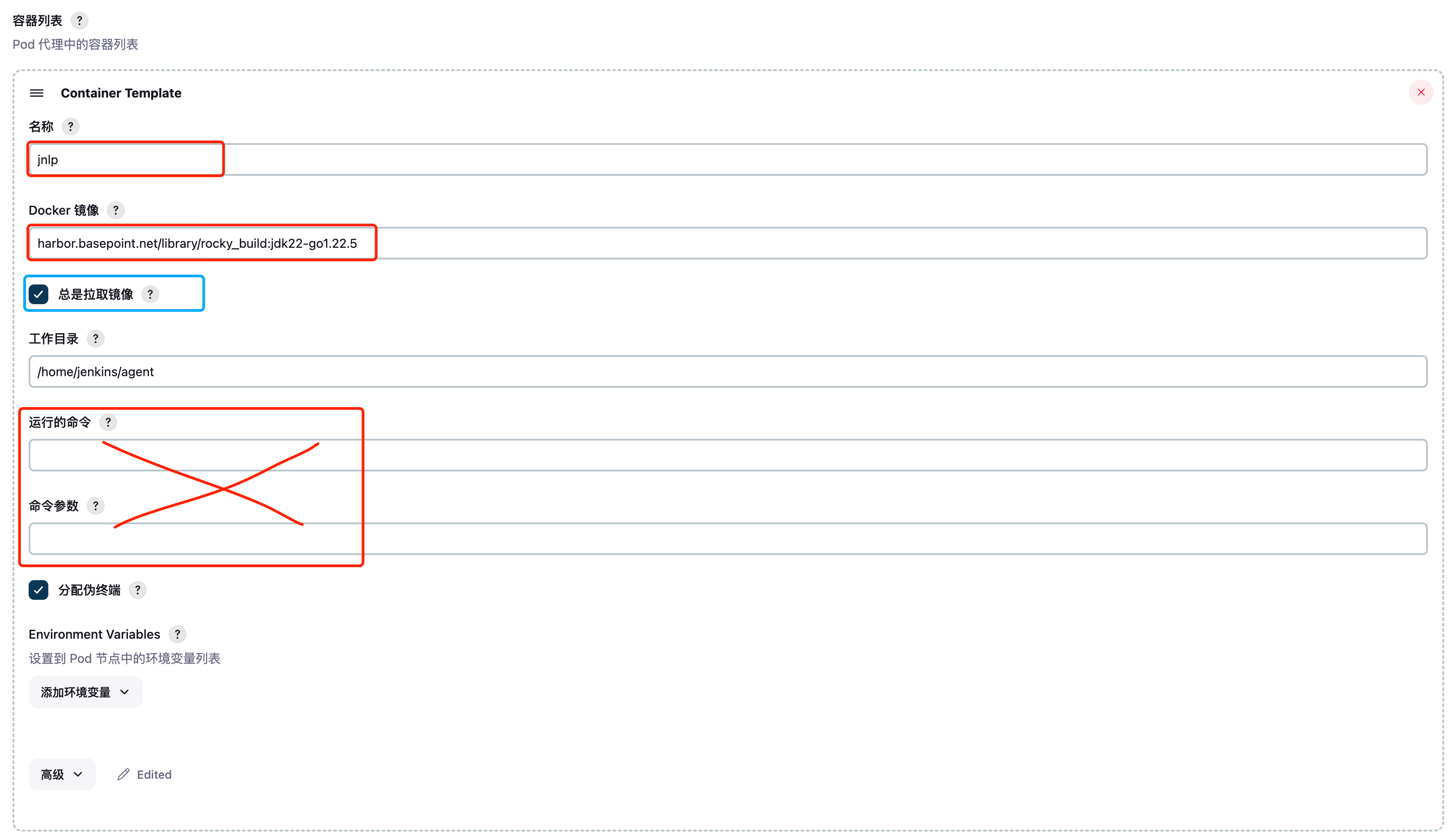
这里使用构建的镜像,jnlp名称是固定的,否则覆盖不了默认的jnlp容器,
运行的命令和参数不要写,否则会替换镜像中的CMD或者ENPTYPOINT参数
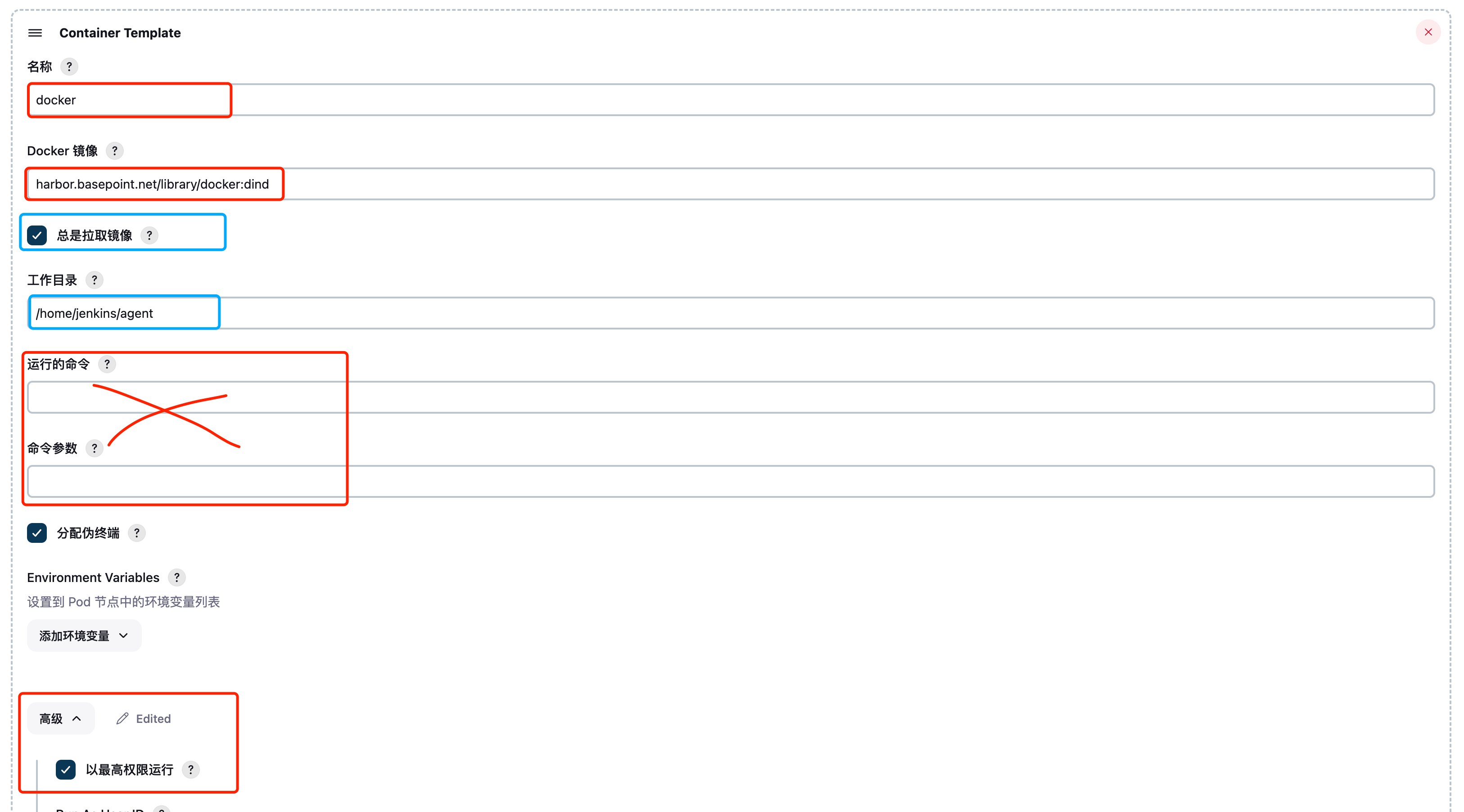
(可选)使用Docker in Docker 构建docker镜像,必须使用最高权限运行,
运行的命令和参数不要写,否则会替换镜像中的CMD或者ENPTYPOINT参数
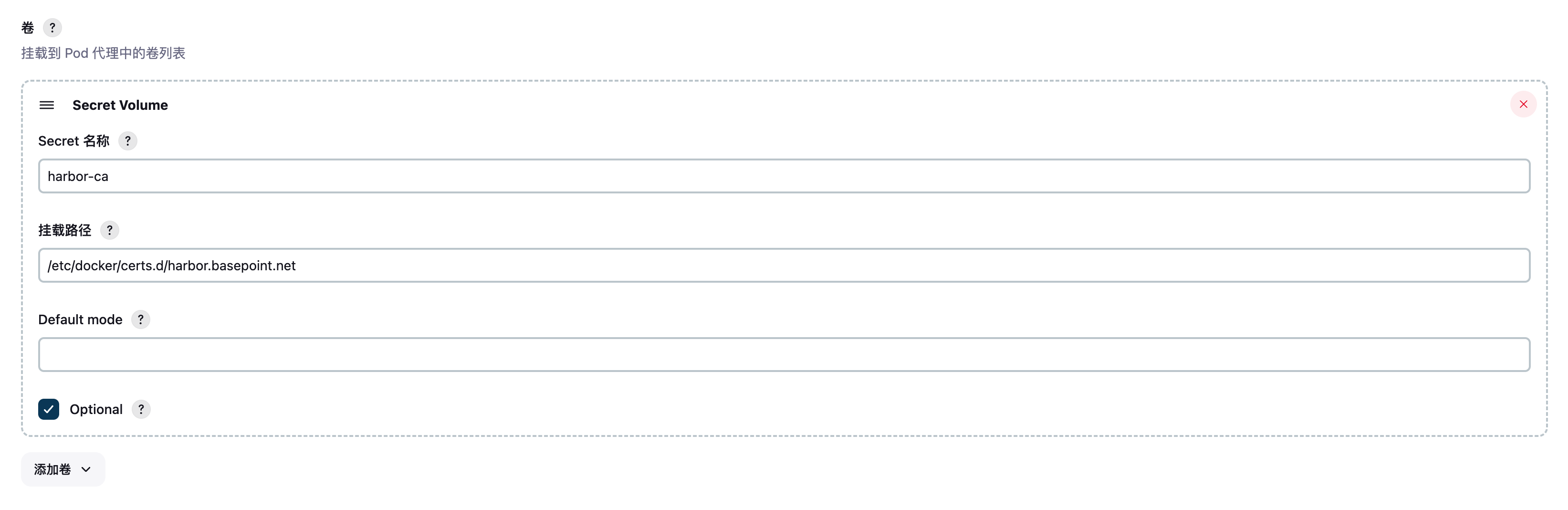
docker容器登录harbor时使用,harbor-ca是使用trust分发的ca.crt
apiVersion: trust.cert-manager.io/v1alpha1 kind: Bundle metadata: name: harbor-ca spec: sources: - secret: # devops-tls是源secret(使用cert-manager创建的自签名证书),包含ca.crt name: "devops-tls" key: "ca.crt" target: secret: key: "ca.crt"cert-manager和trust参考请转移以下文章
原文地址:使用cert-manager 生成自签名证书 - Elijah Blog (sreok.cn)
原文地址:使用trust-manager将TLS证书同步到其他命名空间 - Elijah Blog (sreok.cn)

(可选)pod模版中获取镜像如果是私有镜像需要用到,创建如下:
kubectl create secret docker-registry regcred \ --docker-server=harbor.basepoint.net \ --docker-username=admin \ --docker-password=Harbor12345 \ --docker-email=admin@basepoint.net -n devops
创建pipeline项目(golang后端)
pipeline {
agent {
// 与pod模版设置的标签一致
label 'slave'
}
stages {
stage('Git Clone') {
steps {
container("jnlp"){
//git branch: "main", credentialsId: "gitlab-root", url: "http://gitlab-webservice-default.devops.svc:8181/kube-go/kube-go.git"
git branch: "main", credentialsId: "gitlab-root", url: "https://gitlab.basepoint.net/kube-go/kube-go.git"
}
}
}
stage('GO Build') {
steps {
container("jnlp"){
echo 'go编译'
sh 'go version'
sh 'go mod tidy'
sh 'go build -o ./build/ ./main/main.go'
}
}
}
stage('Docker Build') {
steps {
container("docker"){
echo '构建docker镜像'
sh 'docker -v'
// 登录harbor私有仓库
sh 'docker login harbor.basepoint.net -u admin -p Harbor12345'
// FROM镜像不使用/etc/docker/certs/下的证书,提前拉取Dockerfile中的FROM镜像
sh 'docker pull harbor.basepoint.net/library/golang:1.22.5'
sh 'docker build -t harbor.basepoint.net/kube-go/kube-go:v1 .'
}
}
}
stage('Docker Push') {
steps {
container("docker"){
echo '推送docker镜像'
sh 'docker push harbor.basepoint.net/kube-go/kube-go:v1'
}
}
}
}
post {
always{
script{
println("流水线结束后,经常做的事情")
}
}
success{
script{
println("流水线成功后,要做的事情")
}
}
failure{
script{
println("流水线失败后,要做的事情")
}
}
aborted{
script{
println("流水线取消后,要做的事情")
}
}
}
}测试构建
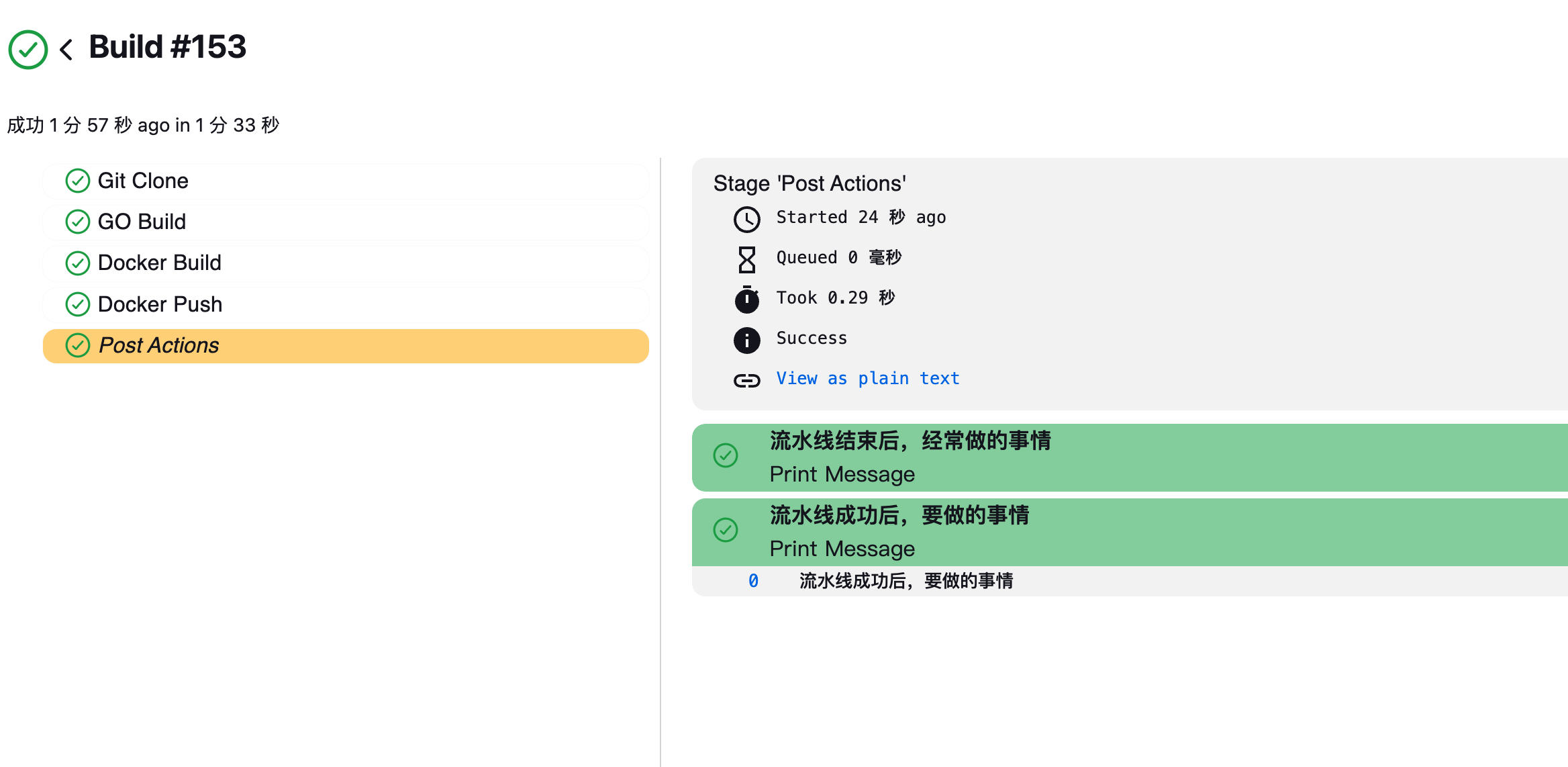
查看构建之后的镜像